Essential Eight: A Guide to the ACSC’s Cybersecurity Framework
Cyberthreats are a major cause for concern for businesses today, not only because they are growing in frequency but also because they are becoming more sophisticated and damaging. According to cybersecurity experts, it’s not a matter of “if” an organisation or an entity will experience a cyberattack but “when” the attack will happen. The harsh reality is no organisation is immune to cyberattacks. So, what is the solution to this unceasing menace?
While cybersecurity threats continue to be the biggest challenge businesses face today, with the right tools and strategies, you can help clients build resilience and mitigate these risks effectively. In this article, we’ll deep dive into the Australian Cyber Security Centre’s (ACSC) Essential Eight, a pragmatic framework designed to help businesses mitigate cyber-risks efficiently. This article will provide an overview of the Essential Eight and explain how its implementation can help fortify your and your clients’ cybersecurity posture.
What is the Essential Eight?
The Essential Eight is a set of eight baseline strategies recommended by the Australian Cyber Security Centre to help organisations protect against cyberthreats. These strategies are designed to prevent cyberattacks, limit the impact if they occur and ensure quick recovery. When implemented correctly, these strategies will help enhance an organisation’s cybersecurity posture and protect against common cyberthreats.
Why implement the Essential Eight security controls?
Implementing the Essential Eight security controls is not just a technical necessity but a strategic move to secure business operations, protect sensitive information and ensure resilience against cyberthreats.
The Essential 8 provides a comprehensive approach to cybersecurity by focusing on three primary objectives: preventing cyberattacks, limiting their impact and ensuring data recovery and availability. Here’s a closer look at each of these objectives:
- Prevent cyberattacks: The Essential Eight’s foremost objective is to prevent cyberattacks by implementing strategies such as application control/whitelisting, regular patching of applications, configuring macro settings in Microsoft Office and hardening user applications.
- Limit cyberattack impact: Despite best efforts to prevent them, some cyberattacks may still succeed. The Essential 8 addresses this by limiting the potential impact by restricting administrative privileges, patching operating systems and adding multifactor authentication (MFA).
- Data recovery and availability: In the event of a successful attack, the ability to recover and maintain data availability is crucial. Daily backups, a core component of the Essential Eight, ensure that critical business data can be restored quickly after an incident.
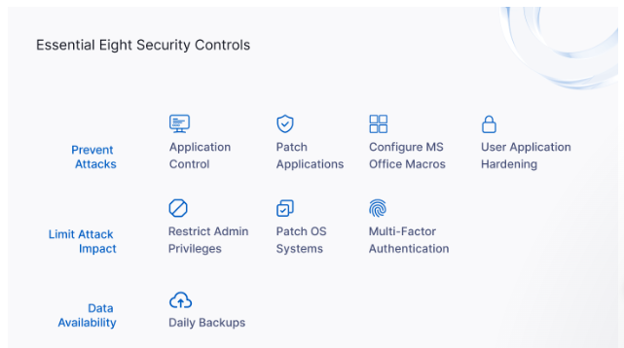
Figure 1: The Essential Eight security controls
Benefits of implementing the Essential Eight
Adopting the Essential Eight strategies can provide several key benefits, including:
- Enhanced security: By addressing common attack vectors, businesses can significantly reduce their exposure to cyberthreats.
- Regulatory compliance: Following the Essential 8 can help organisations meet various regulatory requirements and standards, showcasing their commitment to cybersecurity.
- Cost efficiency: Preventing incidents is often more cost-effective than dealing with the aftermath of a breach.
- Reputation management: Demonstrating robust cybersecurity practices can enhance an organisation’s reputation and trustworthiness with clients and partners.
Is the Essential Eight mandatory?
The Essential Eight is primarily a set of recommended strategies rather than a mandatory regulation or legal mandate. It serves as a framework aimed at guiding organisations in implementing effective cybersecurity measures. Adhering to the Essential Eight is highly recommended but voluntary for most private-sector businesses.
However, the Essential 8 (maturity level 2) is mandatory for non-corporate Commonwealth entities in Australia. The Essential Eight is incorporated into the Australian Government’s Protective Security Policy Framework (PSPF). These policies outline the minimum security requirements that Commonwealth entities must adhere to, ensuring consistent and effective security measures across the government. The Australian Cyber Security Centre also provides guidance and support to these entities to help them achieve and maintain compliance.
What are the Essential Eight mitigation strategies?
As discussed in the section above, the Essential 8 strategies are divided into three objectives: Prevent, Limit and Recover. Here’s an overview of the Essential Eight mitigation strategies:
Preventing cyberattacks
The first objective of the Essential 8 is to prevent cyberattacks by strengthening the initial defences of a company’s IT infrastructure.
- Application control/whitelisting: Application control or whitelisting involves allowing only approved applications to run on a company’s systems. This prevents the execution of malicious software, including ransomware and other unauthorised programmes.
- Patch applications: Regularly updating software applications is crucial. This involves applying security patches to fix vulnerabilities that cybercriminals could exploit.
- Restrict Microsoft Office macros: Macros can be exploited to deliver malware. To significantly reduce this risk, businesses must configure the macro settings to block macros from the internet and only allow those macros that have been assessed.
- User application hardening: This control involves disabling or restricting features in applications that are not necessary for business functions but could be exploited, such as Flash content, Java and ads.
Limiting attack impact
The second objective of the Essential 8 security controls is to reduce the damage caused by breaches.
- Restrict administrative privileges: Administrative accounts should be limited and monitored. Users should only have the privileges necessary for their role to reduce the risk of these accounts being compromised and used to facilitate further attacks.
- Patch operating systems: Operating systems should be kept up to date with security patches, just as applications. This includes deploying patches for critical vulnerabilities within 48 hours to defend against potential exploits.
- Multifactor authentication: MFA provides additional security by requiring two or more verification methods for system access. This greatly reduces the risk of unauthorised access, even if passwords are compromised.
Ensuring data recovery and availability
The third objective is to ensure swift restoration of critical data and maintain business continuity in the event of a cybersecurity incident.
- Regular backups: Regular backups are essential for recovery in the event of data loss due to cyber incidents, such as ransomware. Backups should be kept separate from the network and tested regularly to ensure they can be restored.
What is the Essential Eight Maturity Model?
The Essential Eight Maturity Model helps organisations assess their cybersecurity maturity and improve their security posture. It provides a structured approach to implementing the Essential 8 strategies, allowing businesses to progressively enhance their security measures. The model is divided into four maturity levels, each representing a different stage of implementation and effectiveness.
Maturity level zero
Maturity level zero indicates that an organisation has a weak cybersecurity posture, with either no implementation of the Essential Eight strategies or only minimal progress made. At this level, the organisation is highly vulnerable to cyberthreats, as basic security controls are either absent or insufficient. This level highlights the need for immediate action to establish foundational cybersecurity practices.
Maturity level one
Maturity level one focuses on mitigating an organisation’s common security weaknesses that threat actors can easily exploit, such as an unpatched vulnerability or weak passwords. This level represents the initial stage of implementing the Essential Eight strategies. At this level, organisations have started to implement basic security measures but may not have fully integrated them into their processes. This level shows a commitment to improving cybersecurity but indicates that further work is needed to achieve robust protection.
Maturity level two
Maturity level two focuses on building resilience against attackers who use stronger attack techniques to bypass security systems and evade detection. This level signifies a more advanced stage of implementation where the Essential Eight strategies are systematically applied and integrated into the organisation’s operations. Organisations at this level have a solid defence against cyberthreats but can still enhance their measures for maximum effectiveness.
Maturity level three
Maturity level three aims to prevent malicious actors who employ sophisticated methods to exploit potential gaps in the target’s security defences. This level represents the highest level of maturity in the Essential Eight model. At this stage, organisations have fully integrated and optimised the Essential Eight strategies into their cybersecurity framework, providing the highest level of defence against cyberthreats. Organisations at this level are well-equipped to defend against a wide range of threats.
What should be considered when implementing Essential Eight?
When implementing the Essential 8 cybersecurity strategies, organisations should carefully consider several critical factors to effectively and progressively enhance their cybersecurity posture.
Businesses should determine their current maturity level for each of the Essential 8 strategies. This helps in understanding the starting point and identifying areas that require immediate attention. This baseline assessment also helps to understand the differences between the current state and the desired maturity level.
Establish clear, attainable goals for progressing through the maturity levels. Implement all eight strategies in a balanced manner, aiming to achieve the same maturity level across all strategies before advancing to higher levels.
Organisations should adopt a risk-based approach when implementing the Essential Eight, which means they should understand the risks they are exposed to and take appropriate actions with regard to their risk level. To do this effectively, they should strive to reduce exceptions (temporarily bypassing security policies or controls due to strategic factors) and their impact by applying alternative controls and keeping the number of affected systems or users as low as possible.
Businesses should conduct regular assessments to monitor progress against the maturity level and make adjustments and improvements.
While the Essential Eight provides a solid foundation, organisations should consider additional strategies and controls beyond minimum preventative measures.
Unlock actionable insights from our expert panel on the Essential Eight Framework and NIST standards. Watch the on-demand webinar to learn practical steps to integrate core cybersecurity frameworks into your strategy.
How does Datto help?
Implementing the Essential Eight framework is crucial for building resilience against a variety of cyberthreats. One of the core strategies within this framework is ensuring regular backups. Datto offers a comprehensive suite of backup and recovery solutions that support this essential strategy, helping you safeguard your clients’ critical data and ensure business continuity. Here’s how Datto’s solutions align with the Essential Eight’s “regular backups” strategy:
Datto allows you to customise the backup interval/recovery point objective (RPO) for your appliances, ensuring that your backup schedule aligns with your clients’ specific business needs.
With Datto Backup for Microsoft Azure and Endpoint Backup with Disaster Recovery, Datto provides an automatic, hourly backup schedule to meet aggressive RPO goals. Similarly, Datto Endpoint Backup solutions provide automatic backups every two hours, further supporting stringent RPO requirements and minimising data loss risks.
For data within Software-as-a-Service (SaaS) applications, such as Microsoft 365 and Google Workspace, Datto SaaS Protection performs three daily backups. This frequent backup schedule ensures your clients’ mission-critical data is always up to date and recoverable.
Figure 2: Datto data protection for every use case
Additionally, Datto backup appliances are designed to operate outside the Windows attack surface, providing an additional layer of security against potential attacks and ensuring that your backup data remains protected.
Support Essential Eight implementation with Datto
Datto supports MFA/single sign-on (SSO) capabilities in the Datto Partner Portal for enhanced security and user experience. MFA adds layers of verification, making unauthorised access harder, while SSO reduces password vulnerabilities and adds convenience.
Role-based access control (RBAC) safeguards sensitive information and resources by restricting access to only authorized personnel. The Local Users control panel allows you to assign role-based feature and functionality access to local user accounts on the Datto appliance. You can define which people in your organisation have administrative access to your Datto devices and which functions they are allowed to perform.
The Datto Cloud’s immutable design provides maximum security and reliability for MSP clients. It provides multiple security layers to protect client data, including a team of in-house security professionals, mandatory two-factor authentication (2FA), hardened backup appliances, geographically distributed data centres, Cloud Deletion Defense™, AES-256 encryption in flight and optional encryption at rest.
Datto’s Cloud Deletion Defense™ allows users to regain access to deleted cloud snapshots when an agent is either mistakenly or maliciously deleted. When agents are deleted, the associated cloud snapshots are normally deleted too. Cloud Deletion Defense™ provides a window to recover this cloud data.
Automatic, daily screenshot verification confirms that your Datto device’s backups are healthy and working. This feature allows MSPs to not only see if the backed-up system is bootable but also provide the ability to verify that applications are accessible.
Datto’s Advanced Verification allows MSPs to enable and schedule a suite of automated integrity checks to evaluate and report backup health. By leveraging Screenshot Verification, Local Verification, Application and Service Verification, and building in support for customer verification scripts, this feature aggregates a wide array of customisable health information about the integrity of your backups.
Datto’s groundbreaking 1-Click Disaster Recovery (DR) feature makes disaster recovery incredibly quick and effortless. The innovative feature allows MSP technicians to clone virtual machine and network configurations from previously conducted successful DR tests, eliminating the need to repeat manual and complex configuration processes.
Integrating Datto’s robust backup and recovery solutions into your cybersecurity strategy can strengthen your clients’ resilience against evolving cyberthreats. Request a demo today!




