What Is Business Email Compromise (BEC)?
In today’s fast-paced digital world, the threat of business email compromise (BEC) looms larger than ever. Imagine a scenario where a seemingly innocuous email from a senior-level executive requests an urgent fund transfer. Since the message is from a person of authority and seems urgent, you make that transfer. However, you soon realize that the person’s email was compromised, and you inadvertently wired funds into the hands of cybercriminals. This is just one example of how BEC, a sophisticated form of cybercrime, is wreaking havoc in the business landscape.
BEC scams — a particular form of phishing attack — involve attackers impersonating trusted entities to manipulate individuals into transferring funds or divulging sensitive information. These scams are on the rise today, especially thanks to the growing remote workforce. In 2022, the Federal Bureau of Investigation (FBI) received more than 21,000 BEC complaints, with estimated losses totaling more than $2.7 billion.
Since BEC scams are difficult to detect and prevent, managed service providers (MSPs) must be more vigilant than ever to defend against them. Even if you are leveraging an advanced threat protection (ATP) solution, your clients’ business-critical data might still be vulnerable to BEC attacks. That’s where Datto SaaS Defense can be your game changer. See how SaaS Defense’s data-independent technology helps you proactively defend against all malware, phishing and BEC attacks.
Now, let’s find out more about how BEC attacks work and what best practices you can follow to fortify your clients’ defenses against this growing menace.
What is business email compromise (BEC)?
Business email compromise is a type of phishing attack where the attacker forges a genuine-looking email message to trick the victims. Posing as a trusted figure within the organization, the attacker manipulates the victim into divulging sensitive information or performing unauthorized actions, such as fund transfers.
BEC attacks, also commonly referred to as email account compromise (EAC), are more specific and personalized than standard phishing emails, making them harder to detect. They are tailored to target specific individuals and might impersonate someone the intended victim corresponds with regularly over email. These attacks could also be free of malicious links, attachments or anything that could trigger an email security filter.
For instance, in BEC attacks, cybercriminals impersonate high-level executives, such as the CEO or CFO of an organization, to deceive employees into sharing sensitive financial information or doing immediate fund transfers or gift card purchases. By posing as an authoritative figure, the attackers aim to instill a sense of urgency and importance in their requests while reducing suspicion, thus increasing the likelihood of the victim complying with their demands.
What is the main goal of business email compromise?
The main objective of BEC attacks is financial gain. Cybercriminals carry out BEC attacks by manipulating individuals into transferring funds, disclosing sensitive information or performing actions that directly contribute to their monetary goals. However, an alarming aspect of these attacks is the use of stolen information as a launchpad to carry out further attacks and scams.
Attackers can use stolen personally identifiable information (PII) to target the customer base of the organization and launch additional scams and fraudulent activities. They can use the PII to perpetrate identity theft, financial fraud or even carry out targeted attacks on customers. The ripple effect of such attacks has the potential to cause irreparable damage to a business. Beyond immediate financial losses, the compromise of PII triggers a cascade of consequences — damaged customer trust, regulatory scrutiny and potential legal repercussions.
How does business email compromise work?
BEC attacks are designed to deceive people by using social engineering and impersonation techniques. Typically, BEC scams involve email or website spoofing, where the attacker makes minor changes to a legitimate company email or website address in order to trick users into opening the email and taking some action. BEC scams also make use of compromised email addresses, so the email may actually come from a legitimate email address.
What are some identifiers of a BEC attack?
To help you detect a BEC attack, here are some signs to watch out for:
Time urgency
BEC attacks often create a sense of urgency to manipulate targets into quick action. It could be an urgent email from a seemingly high-ranking executive requesting last-minute changes or a quick personal favor. The requests could also be timed to arrive at the end of the workday or week, further putting pressure on the targeted employees to complete the tasks before the end of business hours.
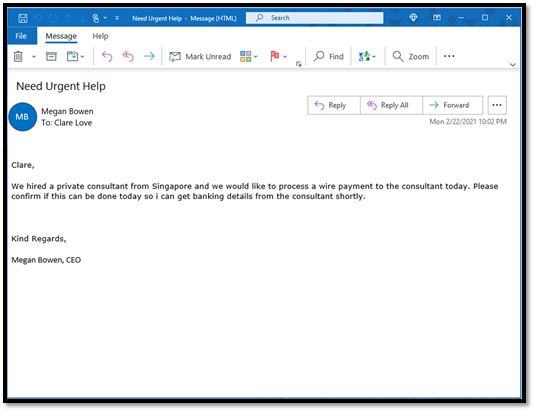
Covert requests
BEC emails often appear as ordinary or harmless messages, which can deceive the recipient into thinking they are safe. By blending into the fabric of everyday communication, these emails evade immediate suspicion and often seek sensitive information or unauthorized actions. For example, it can be a seemingly routine email from a colleague requesting sensitive employee payroll information.
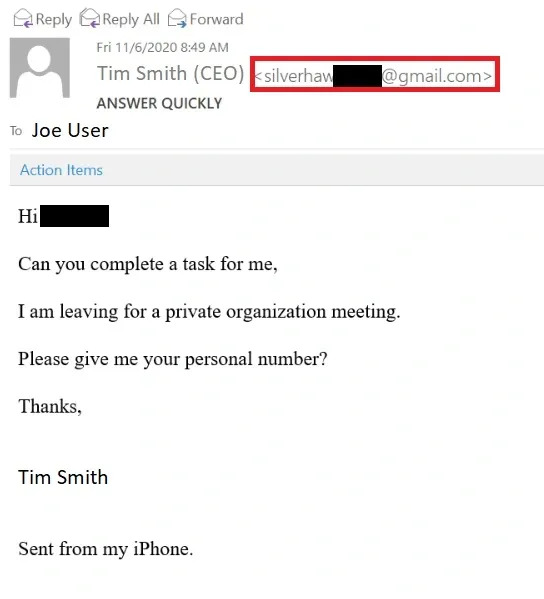
Mobile and personal mailboxes
Threat actors may use a common tactic of impersonating an executive’s personal email address, like a Gmail account, to bypass existing security measures. These emails could contain last-minute requests that ask the recipient to do a favor. Such emails often have a stock signature, which creates the illusion that the email was sent from the executive’s mobile phone.
Supply chain spoofing
Another common tactic in BEC attacks is the use of supplier or vendor identities. Attackers assume the identities of supply chain partners or vendors to circumvent any internal processes. These types of messages can be identified by their direct nature, such as a request from the supplier to abruptly change shipping information without following the proper procedures.
Who is usually targeted by a BEC attack?
Now that we know what some identifiers of a BEC attack are, let’s look at some roles and profiles in an organization that are usually targeted by BEC scams.
Owners, executives and leaders
High-profile individuals are often targeted for their authority and access to critical financial information. Such attacks on leaders can have cascading effects on the entire organization, affecting strategic decisions and financial stability.
Finance employees
Individuals with access to payment systems and sensitive financial data are targeted for financial fraud, resulting in significant losses for organizations.
HR employees
HR professionals may be targeted for access to employee data, which could lead to identity theft and further attacks. Compromised employee information leads to targeted attacks on staff.
New or entry-level employees
Inexperienced employees may be targeted due to their potential vulnerability and unfamiliarity with security protocols. Exploiting newcomers may provide access to internal systems, compromising sensitive information and potentially exposing security weaknesses.
Common types of business email compromise
Let’s explore different types of BEC attacks that can pose a significant threat to organizations. It is crucial for organizations to understand these different types of attacks in order to better protect themselves against the multifaceted challenges these attacks can present.
Owner/CEO fraud
It is easy for cybercriminals to impersonate high-level executives and leaders in a BEC scam since their details are often publicly available on various platforms. These fraudulent emails appear genuine and use the authority of the impersonated person to create a sense of urgency, tricking employees into revealing sensitive information or making unauthorized fund transfers.
False invoice scams
In these bogus invoice emails, cybercriminals will spoof an employee’s email account that is authorized to process invoice payments or mimic a familiar supplier. The attacker will then use this account to ask another employee to transfer the funds or pay an invoice.
Account compromise
In this case, the attacker gains unauthorized access to an employee’s account and gathers the contact list of company vendors, partners and suppliers. The hacker will then connect with these contacts, requesting payments to be processed to a fake account.
Attorney impersonation
Cybercriminals often impersonate an organization’s attorney or a legal professional to contact C-level executives or employees. These deceptive communications pressure recipients into divulging sensitive information or initiating unauthorized actions, often resulting in financial losses. The attackers often do it at the end of the business hours so as to put pressure on the victim.
Data theft
Some BEC attacks extend beyond financial motives, with a focus on stealing sensitive data or PII. Attackers later exploit this compromised information to launch a wider cyberattack on the company and its customer base, resulting in irreparable damage to the brand’s reputation and customer relationships.
Real-world examples of business email compromise
Now, let’s dive into some real-life examples that showcase the impact of BEC scams. These stories offer practical insights into the strategies leveraged by cybercriminals during BEC attacks.
Tech giants conned out of $121 million
A few years ago, the business world was taken aback by news of a Lithuanian international conning tech giants Google and Facebook out of millions through a BEC scam. Between 2013 and 2015, a cybercriminal group led by Evaldas Rimasauskas sent fake invoices impersonating a Taiwanese tech manufacturer and extorted more than $121 million from the Silicon Valley tech giants.
The gang carried out this scam by sending fraudulent BEC emails to employees and agents of the victim companies, which regularly conducted multimillion-dollar transactions with the Asia-based manufacturer.
Toyota subsidiary loses $37 million
In 2019, in a not-so-sophisticated BEC scam, cybercriminals tricked a Toyota employee to wire millions to a foreign account. As part of the scam, hackers sent BEC emails to employees in the finance and accounting department of the Toyota Boshoku Corporation, a European subsidiary of Toyota. The emails requested fund payment into a specific bank account controlled by the hackers. One employee fell for this scam, wiring $37 million to the hackers’ account.
Classic example of CEO fraud
Scoular, a U.S.-based grain trading and storage company, fell victim to a CEO fraud BEC scam a few years ago. In June 2014, a corporate controller of the company received a seemingly top-secret email from the CEO. The chief executive instructed the employee to work with a KPMG lawyer since they were about to acquire a Chinese company. Consequently, the employee transferred $17.2 million to an account in China, only to later realize that it had been a scam.
Puerto Rico government almost loses $4 million in a BEC scam
In 2020, the Puerto Rico Industrial Development Company (PRIDCO) received an email that prompted one employee to transfer $4 million to a fraudulent account in the U.S. However, the FBI swiftly froze the money sent, which also involved public pension funds. This attack underlines that BEC is a major threat to organizations of all sizes and across all sectors, including non-profit organizations and government agencies.
How to prevent business email compromise?
Since we now have a clear picture of what a BEC scam is and how it works, let’s look at some proactive measures and key strategies that could help you prevent BEC attacks to a great extent.
Employee training and awareness programs
Employees are the first line and often the weakest link in a company’s cyberdefense. It is thus critical to equip them with the necessary skills to identify phishing attempts, recognize social engineering tactics and understand the critical role they play in maintaining a secure IT environment. Regular awareness sessions can foster a vigilant workforce, mitigating the risk of falling victim to BEC schemes.
Email authentication and security measures
It is equally important to implement robust email authentication protocols and security measures that can verify the legitimacy of incoming emails. Combining these measures with advanced email security solutions will help you to filter out malicious content. This also reduces the likelihood of successful email impersonation.
Do you want to stop BEC attacks at their roots? Download the Enterprise Strategy Group’s technical review of Datto SaaS Defense and find out how it helps organizations effectively defend against zero day threats and other cyberattacks.
Multifactor authentication and password policies
Enabling multifactor authentication (MFA) for all email accounts is crucial for enhancing security. It adds an extra layer of protection that prevents unauthorized access, even if login credentials are compromised. In addition, it is important to establish strict password policies that require complex and regularly updated passwords. These measures can significantly strengthen the defense against unauthorized access to email accounts.
Secure payment platforms and verification
It is crucial to ensure the safety of financial transactions by utilizing secure payment platforms and implementing a strong verification process. Establishing clear procedures for validating payment requests, especially those received via email, is recommended. Confirming the legitimacy of payment instructions through secondary verification channels prevents BEC threat actors from manipulating financial transactions.
What to look for in a business email compromise solution?
While best practices provide a solid foundation, BEC threats are evolving at a rapid rate and necessitate more than just preventive measures. It’s crucial to acknowledge that even the most diligent efforts might not be foolproof. This is where a robust ATP solution like Datto SaaS Defense steps in. Datto SaaS Defense for Microsoft 365 offers comprehensive protection against malware, ransomware and phishing attacks like BEC. Here are some crucial aspects you need to look for in a BEC solution and how SaaS Defense ticks all those boxes.
Zero day attack protection
BEC attacks are rapidly evolving, and your solution must be robust and proactive enough to defend against the most advanced threats. Traditional email security solutions depend on data from previously detected cyberthreats and successful penetration tactics, which leaves gaps in protection that new threats could exploit. However, Datto SaaS Defense is unique. SaaS Defense’s data-independent technology was developed by security experts to detect and stop zero day threats that other solutions miss.
Attachment scanning
A robust BEC solution should conduct thorough scans of email attachments to identify potential threats hidden within files. On that front, SaaS Defense conducts comprehensive scanning of all types of malicious attachments, including malicious files that require a password for accessing them, malicious payloads that can stay harmless until triggered, macro malware that takes advantage of visual basic for applications (VBA) programming in Microsoft 365 macros, WMI commands, etc.
Link scanning
Like malicious attachments, SaaS Defense also scans emails for phishing links. If there is a malicious attachment or phishing link in an email, the solution will replace the email with a stub that says it is a malicious threat and advise end users to contact their IT provider if they think it is a mistake. SaaS Defense also gives end users the capability to go into their junk folder to see the email that came in and got blocked by the system.
Minimal user interaction time
Time is of the essence in cybersecurity, and you need a solution that swiftly detects and neutralizes threats before they reach the end user’s inbox. Datto SaaS Defense is built from the ground up to prevent zero day threats as soon as they are encountered, drastically minimizing detection and user interaction time.
How can Datto help you with business email compromise?
From identifying the subtle nuances of BEC attacks to implementing best practices and key preventive strategies, we’ve discussed how you can protect your clients from BEC attacks. And now, for the ultimate defense, consider adding Datto SaaS Defense for Microsoft 365 to your portfolio.
Datto SaaS Defense is a comprehensive threat protection solution for Microsoft 365. With SaaS Defense, MSPs can proactively detect and defend against BEC attacks and zero day threats across the complete Microsoft 365 suite, including Exchange, OneDrive, SharePoint and Teams. Its data-independent technology detects unknown and zero day threats by analyzing the composition of a safe email, chat or document rather than scanning for already known security threats.

Datto SaaS Defense proactively monitors and eliminates cyberthreats as soon as they are encountered, without manual interference or end-client disruption. Moreover, its robust monitoring allows you to demonstrate product value to clients with simple, detailed reporting that articulates why a threat was identified as malicious.
When tested by Miercom, a global leader in independent product testing, SaaS Defense detected 96% of the malware threats delivered by Microsoft 365 applications, catching threats that were missed by native Microsoft security. In that test, SaaS Defense proved 91% detection efficacy for business email compromise threats, outperforming competition by at least 29%.
Purpose-built for MSPs, Datto SaaS Defense is the best solution for MSPs to protect their clients’ Microsoft 365 data from BEC threats and other cyberattacks. Learn more about Datto SaaS Defense today.




