What Is Social Engineering?
Cybersecurity is one of the biggest challenges businesses face today. Unfortunately, rapid technological advancements, such as artificial intelligence (AI) and machine learning (ML), have made cyberthreats even more dangerous and challenging to manage.
Cybersecurity primarily revolves around technology, people and processes; however, people are often considered the weakest link in the cybersecurity chain. According to Verizon’s 2023 Data Breach Investigations Report, more than 70% of breaches involved the human element, which includes social engineering attacks, errors and misuse. It’s no secret humans make mistakes and are emotional beings. They are also the entry points to your organization’s systems and data.
Threat actors take advantage of these weaknesses and opportunities to launch cyberattacks by means of social engineering. It is perhaps the most popular cyberattack technique threat actors use to manipulate human behavior to gain access to an organization’s systems and data with great success. According to the 2022 Internet Crime Report produced by the FBI’s Internet Crime Complaint Center (IC3), it received over 800,900 complaints regarding phishing attacks, with losses exceeding $10.3 billion.
Read on to learn more about social engineering, what makes it so effective, how AI makes it even more destructive and how to defend against social engineering attacks.
What is social engineering?
Social engineering in the realm of social and political sciences refers to the concept of manipulating people to change human attitudes or social behavior on a large scale. It attempts to influence people to achieve certain goals or take specific actions effectively and uninterruptedly. Social engineering is a combination of two words: “social,” which symbolizes a group of individuals that form a society, and “engineering,” which means applied science used to resolve human-related problems or social issues, similar to how technical issues are resolved in machines. According to the early concept of social engineering, laws are created to control human behavior or, rather, for the welfare of society. Therefore, any law or governance can be termed social engineering.
What is the goal of social engineering?
The main objective behind social engineering is societal reform. It aims to manage social change by influencing certain human behavior.
Social engineering has been around since time immemorial. Rulers, governments, businessmen, and even ordinary men and women have used social engineering in some form or capacity to manipulate and maneuver social behavior to achieve their goals efficiently. Dutch industrialist J.C. Van Marken introduced the term sociale ingenieurs (social engineers) in one of his essays in 1894. According to Van Marken, the world needs specialists who can handle human (social) problems in the same way technical experts (engineers) deal with machines and processes. His idea of social engineering was to improve people’s lives, and he was the perfect example of a social engineer. For instance, he built a residential park, kindergarten, libraries and social clubs to improve the condition of his employees and their families. Van Marken leveraged social engineering to bring change in his employees’ attitudes/behavior.
Unfortunately, that’s not the case in today’s threat-laden world. Social engineering has become one of the most widely used cyberattack techniques for cybercriminals because it is inexpensive and easy to execute. Social engineering attacks are typically used to win a person’s or persons’ trust to gain access to sensitive information and applications.
Why is social engineering effective?
Humans are naturally helpful and emotional. Social engineering attacks take advantage of these unique human traits and social skills. This type of cyberattack aims to exploit human emotions by creating a sense of fear or urgency and invoking a feeling of greed or guilt. Therefore, a person’s willingness to help could often turn into disastrous situations.
Social engineering is the perfect tool for cybercriminals to appear legitimate while hiding their true selves and motives. They use this tactic to exploit people when they are vulnerable, like when they are stressed or multitasking. Threat actors use important contexts about them or well-crafted messages that resonate with them to lower their defenses. For example, they use languages, tools and methods of communication the victim is familiar with or strategies that threaten their livelihood or make them feel at risk.
Figures 1 and 2 show examples of active credential phishing attacks targeting enterprises with various sophisticated techniques for defense evasion. These campaigns use timely lures relevant to remote work, such as password updates, meeting information and help desk tickets.
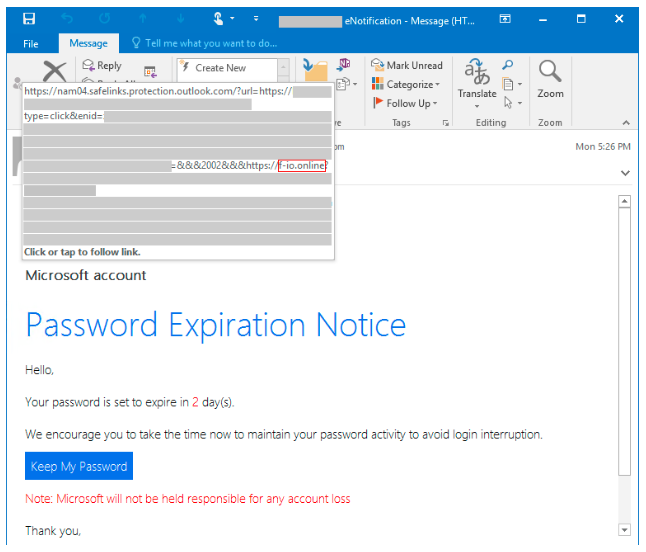
Figure 1. Password expiration notice phishing email. (Source: Microsoft)
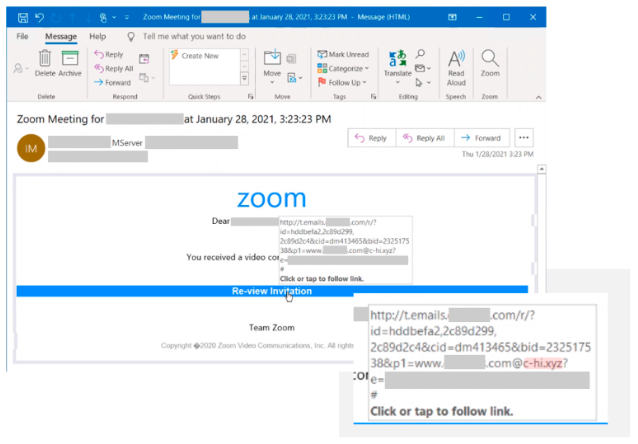
Figure 2. Zoom meeting invite phishing campaign. (Source: Microsoft)
What is a social engineering attack?
Social engineering attack is the process of psychologically manipulating individuals to perform specific actions. Threat actors rely on the social nature of humans to communicate with unsuspecting targets, influence their behavior, and trick them into performing activities or disclosing vital information. They conceal their real identities and motives and present themselves as trusted individuals that the target knows or high-ranking officials in the victim’s organization.
Social engineering attacks aim to exploit human error or weakness by gaining their trust and influencing them, rather than targeting IT vulnerabilities or breaking into an organization’s defense systems, which is much harder and time-consuming. The methods used in social engineering attacks may seem simple, but they are compelling and highly successful. That’s why social engineering attacks are a popular choice among cybercriminals.
An urgent email that appears to be from one of the coworkers requesting confidential information, an email that seems to be from the IT team to update a password immediately or receiving an offer to disclose sensitive business information in exchange for money are all examples of social engineering.
What is the most common social engineering attack?
Phishing is the most common social engineering technique cybercriminals use because it is cheap, effective and easy to implement. According to Verizon’s 2022 Data Breach Investigations Report (DBIR), 36% of all data breaches involved phishing. Phishing campaigns are executed using email and text messages.
Phishing, especially spear phishing attacks, are highly targeted. Spear phishing attacks can easily be modified and tuned to specific victims over time. Phishing campaigns can be designed to target particularly vulnerable groups, such as immigrants, the elderly and people with disabilities. Once threat actors gather critical information about the targets and understand their roles, likes, dislikes, etc., they can launch a customized email campaign against them. This type of phishing attack is typically geared toward executives and other key decision-makers in an organization.
Phishing attacks are the entry points to a large number of cyberattacks and fraud. They can be used to deploy malware or strategically designed to influence the target to perform certain actions that benefit the perpetrator, like visiting harmful websites, opening an infected attachment, sending money to threat actors or disclosing sensitive information that can compromise personal or organizational security.
Social engineering attacks are a nightmare for IT security professionals because they are highly convincing and appear in various forms. Learn more about common types of social engineering attacks.
What are examples of social engineering attacks?
There are many variants of social engineering attacks, but they all have a common theme — manipulating the target to take action. Listed below are a few real-life examples of social engineering.
Medibank: Medibank Private Limited, one of Australia’s largest private health insurance providers, became a victim of a cyberattack in October 2022. The hackers accessed the insurance providers’ internal systems via one of its employees’ stolen login credentials. The incident impacted 9.7 million Medibank customers whose private medical information was released on the dark web.
Microsoft Azure wiper attacks: Earlier this year, Microsoft Threat Intelligence reportedly warned about the Azure wiper attacks by Iranian government-backed advanced persistent threat (APT) actors MuddyWater and DEV-1084. The attackers exploited unpatched internet-facing devices, created admin accounts, deployed web shells and stole login credentials. The perpetrators also used compromised Azure Active Directory accounts with global administrator privileges to cause massive destruction, such as data loss, denial of service (DoS) and data exfiltration.
Rockstar Games: In September 2022, the gaming giant Rockstar Games fell victim to a cyberattack that leaked the source code for Grand Theft Auto 5 and Grand Theft Auto 6. One of their employees clicked on a malicious link, allowing the attacker to gain access to the company’s internal network.
How is AI used in social engineering?
AI-powered solutions, such as ChatGPT, have been a game changer, not just for individuals and organizations but also for cybercriminals. While some argue that AI is not 100% accurate or perfect, multiple evidence indicates that AI can be a powerful tool when prompted correctly.
Joanna Stern, an Emmy Award-winning American technology journalist, conducted an experiment using AI technology to clone herself. She used the AI clone to replace her for a day to assess its capabilities. The result was surprising. Her AI voice clone successfully bypassed her bank’s voice biometric system and also managed to deceive her family and the CEO of Snap Inc. Evan Spiegel.
A highly advanced tool like AI in the hands of cybercriminals can be devastating. It is now much easier to develop a malicious program than ever before. Even those without any programming knowledge can create malicious code with a few strokes of the keyboard. Artificial intelligence automates malware development and other processes like preliminary research and content creation, enabling bad actors to launch attacks at scale.
AI-enhanced tools allow cybercriminals to collect large volumes of information from various sources easily, which can then be used to create highly targeted, personalized messages for spear phishing emails.
Deepfake threats are increasing significantly. According to VMware’s Global Incident Response Threat Report, more than 65% of respondents revealed they had seen deepfakes being used as part of an attack. Threat actors can use AI algorithms to create realistic images, audio and videos to impersonate an organization or a trusted individual to deceive the target into divulging critical information or taking malicious actions.
Since AI algorithms are designed to adapt and evolve over time, threat actors can use these tools to improve their attack tactics to evade security controls or perform malicious activities undetected.
How can AI be used to combat social engineering?
Not all hope is lost on AI — fortunately, it’s not limited to cybercriminals alone. Government agencies, organizations and security professionals also leverage artificial intelligence and machine learning to tackle advanced cyberthreats like social engineering.
Your organization can use AI to identify vulnerabilities in your software, systems or IT infrastructure to prevent disasters from occurring. AI- and ML-powered solutions like security event management (SEM) and security information management (SIM) make threat detection and incident response quicker. According to IBM’s Cost of a Data Breach Report 2023, the average time to detect and contain a breach was 214 days among organizations that used AI and automation, while it was 322 days among businesses that did not deploy these technologies.
Managed service providers (MSPs) can take advantage of innovative cybersecurity solutions like Datto Endpoint Detection and Response (EDR) and Graphus, an automated phishing defense platform, that use AI and ML to recognize advanced threats that bypass traditional spam and antivirus filters, further strengthening their clients’ cybersecurity initiatives.
How can an organization help prevent social engineering attacks?
As discussed in the above sections, social engineering attacks rely on human weakness and error, making them extremely unpredictable. Train your employees on how social engineering works, the telltale signs to watch out for and how to report suspicious activities.
These attack tactics use personalized messages and appear to be from legitimate sources, therefore highly convincing. Develop training programs that include best practices like checking the source before clicking on an email, reading email headers carefully, checking for spoofed URLs by hovering the mouse cursor over them and spelling mistakes. BullPhish ID is a security awareness training and phishing simulation solution that can help reduce your organization’s chance of experiencing a cybersecurity disaster by up to 70%.
Another devious characteristic of social engineering is creating urgency or pressuring the target. Your employees must be wary of such situations and consult their manager or superiors before taking any action.
When you bring AI into the mix, it can bypass traditional security systems like antivirus and remain undetected in your IT environment. Your company’s security policies must include strict guidelines on exchanging information with external parties and using only IT-approved tools for communication and collaboration.
Create internal newsletters to celebrate when your organization successfully identifies and prevents a social engineering attack. This will further build awareness among your employees and strengthen your organization’s security posture.
Defend against social engineering attacks with Datto
Social engineering has many facets, and its tactic varies depending on the motive(s) of the social engineer. One of the main objectives of social engineering attacks is to exfiltrate data, as we have seen in the case of Medibank and Rockstar Games above. Hackers target sensitive data like source code, business blueprints and financial information to steal intellectual property (IP), embarrass an entity or extort ransom from the victims. We also discussed the Azure wiper attack incident where Iranian government-backed hackers were able to successfully access vulnerable systems and completely wipe out all Azure resources in the subscription.
Unfortunately, there’s no one-size-fits-all solution to combat the different types of sophisticated social engineering attacks. That’s why, as an MSP, you need the right set of tools in your tech stack to ensure your clients’ mission-critical data on endpoints and in the cloud is secure.
Datto Endpoint Detection and Response (EDR) enables MSPs to detect and respond to advanced threats quickly and efficiently. Its built-in continuous endpoint monitoring and behavioral analysis deliver comprehensive endpoint defense, giving you and your clients the peace of mind you deserve.
Datto SaaS Protection+ for Microsoft 365 and Google Workspace safeguards valuable SaaS data against permanent loss and ensures quick recovery from ransomware attacks and user error with one-click restore functionality.
Datto Backup for Microsoft Azure is a comprehensive business continuity and disaster recovery (BCDR) solution built exclusively for MSPs like you. It ensures your clients’ workloads in Azure, Microsoft’s public cloud computing platform, are protected and easily recoverable.
Talk to us today to bolster your clients’ security initiatives and confidently defend against social engineering attacks.




